
Use CounterCraft’s automated Cyber Deception technology to detect attacks early - even pre-breach; collect real-time threat intelligence specific to your organization; and proactively protect your organization by adapting your defenses to stop attacks.
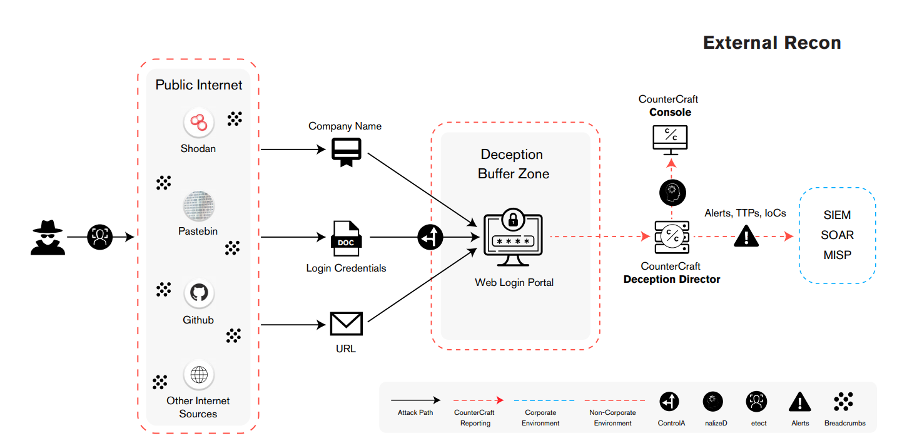
We use social engineering techniques against the attackers. Technical discovery information will be placed where it can be found by a threat actor searching for your organization’s external infrastructure.
The deception buffer zone infrastructure will be hosted on cloud infrastructure. In the deception buffer zone, external services will provide the attackers with a credible target.
When an attacker interacts with the deception buffer zone, an alert is immediately sent from our console and threat intelligence collection starts.
The deliverables are actionable threat intelligence data with enrichments in the form of TTPs (MITRE ATT&CK) and IoCs including IP addresses, and credentials used by threat actors. The threat intel data can be sent to external security tools such as MISP, a SIEM or SOAR platforms.
The goal of the Pre-breach Intelligence Service is to deflect attacks away from the external infrastructure of the organization by deploying a deception buffer zone. The service will deliver real time intelligence that will be used to harden your infrastructure.
Deploy: deploy the assets associated with the service. This includes the creation of the attack vector discovery assets (breadcrumbs), any associated IT assets, and full configuration and deployment of the campaign.
Discover: the threat actors follow a prepared breadcrumb trail to discover and attack external facing services, hosted on your behalf.
Detect: detect when the threat actors are conducting reconnaissance on the deception buffer zone and you will be alerted immediately.
Collect Intel: the platform continues to collect intel in real-time on how the threat actors discovered your infrastructure, and what techniques, tools and procedures they are using to attack. You will be able to access all this information through an easy-to-understand dashboard.
Proactively Protect: make it actionable. Integrate the intelligence gathered with your security infrastructure: e.g. , SOAR, and TIPs.
To understand and stop threats more effectively and efficiently, your existing security infrastructure and people need to work smarter, not harder. ThreatQ is an open and...
Read more
Rapid7 is one of the leading cyber security solutions providers, on a mission to make successful security tools and practices accessible to all. Rapid7 Insight Platform...
Read more
Netwrix Auditor is a visibility and governance platform that enables control over changes,
configurations and access in hybrid cloud IT environments to protect data...
Read more
The affordable, intuitive, easy to implement and manage converged SIEM & SOAR solution of Logpoint extracts events and incidents from the billions of logs existing in any IT...
Read more
Synack helps clients with strategic penetration testing providing full control and visibility, reveals patterns and deficiencies in their security program, enabling...
Read more
Full spectrum cyber deception and ground breaking threat hunting and counterintelligence to detect, investigate and control targeted attacks. The solution combines powerful...
Read more
Swimlane is at the forefront of the security orchestration, automation and response (SOAR) solution market. By automating time-intensive, manual processes and operational...
Read more
DTEX Systems helps hundreds of organizations worldwide to better understand their workforce, protect their data and make human-centric operational investments.
Read more
Armis, the cyber exposure management & security company, protects the entire attack surface and manages an organization’s cyber risk exposure in real-time.
Read more
Halcyon offers a leading solution for protection against Ransomware and other forms of advanced malware. The Halcyon platform is specifically designed to detect, stop, and...
Read more