Threat Intelligence Platform
To understand and stop threats more effectively and efficiently, your existing security infrastructure and people need to work smarter, not harder. ThreatQ is an open and extensible threat intelligence platform that accelerates security operations through streamlined threat operations and management. The integrated, self-tuning Threat Library™, Adaptive Workbench™ and Open Exchange™ allow you to quickly understand threats, make better decisions and accelerate detection and response.

ThreatQ
Empowers security teams to make better decisions.
- Enrich data with context
- Prioritize based on your risk profile
- Accelerate detection and response
- Collaborate across teams
Enrich Data with Context
Correlate external and internal data to gain context and determine relevance and priority.
Prioritize Based on Your Risk Profile
Automatically score and prioritize threat intelligence based on your parameters.
Accelerate Detection and Response
Automate aggregation, operationalization and use of threat intelligence across all systems and teams.
Collaborate Across Teams
Centralize threat intelligence sharing, analysis and investigation in a threat intelligence platform all teams can access.
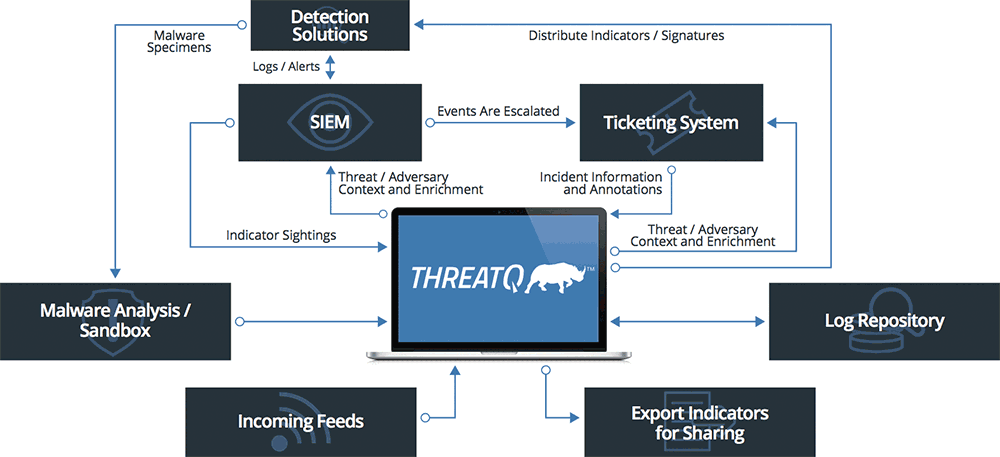
ThreatQ Solution Architecture
ThreatQ is an open and extensible threat intelligence platform, supporting both standard and custom integrations with feeds and security systems. Through these integrations the platform automates the aggregation, operationalization and use of threat intelligence across the entire security infrastructure, supporting multiple use cases, increasing security effectiveness and accelerating security operations.
Threat Intelligence Platform Use Cases, powered by ThreatQ
Threat Data Aggregation
Combine, normalize and contextualize threat data from both external and internal sources automatically into a single, customized and prioritized Threat Library to be used by teams across the organization.
Curated Threat Intelligence
Turn threat data into threat intelligence through context and automatically prioritize based on user-defined scoring and relevance.
Spearphishing
Investigate spearphishing attacks and track over time using the data to improve your defensive posture.
Intelligence Pivoting
Utilize campaign, malware and indicator knowledge to identify related attacks and adversaries that may affect your operations.
Breach Investigation
Support scoping and remediation by correlating artifacts of an investigation with a threat library of related indicators and context.
Vulnerability Scanning
Pivot between a vulnerability, an IOC and an event to more quickly stop threats that take advantage of known security weaknesses.
Threat Hunting
Empower your teams to proactively search for malicious activity that has not yet been identified by your sensor grid.
Improve Incident Response
Global visibility to adversary tactics, techniques and procedures improves remediation quality, coverage and speed.
Strengthen Sensor Grid
Make firewall, IDS, IPS, SIEM and other devices smarter with the most accurate and relevant threat data.
Operational ROI
Retrospectively evaluate your threat intelligence sources’ value, versus the relevance of their information to incidents you experience.
For more information, call our security consultants at +31 (0) 345 506 105 or send an email to info@isoc24.com









