What is Threat Intelligence and why is it important?
In recent years, cyberthreat intelligence has become an important supporting pillar in a mature cybersecurity strategy. When applied well, threat intelligence can help security teams defend against an ever-more sophisticated threat landscape before, during and after attack. By studying adversaries and understanding their strategies and objectives, organizations can build more effective, more refined and more robust cyberdefenses.
The challenge, as will be outlined in this series, is to understand how threat intelligence can be used to help organizations of all sizes strengthen their security posture and accelerate security decision-making processes. With a smarter and more targeted response to cyberthreats, organizations can allocate (often scarce) security resource more efficiently, proactively getting ahead of future attacks and raising the barrier to entry for cybercriminals intent on breaking in.
There is of course no one-size-fits all approach to cybersecurity as a whole, let alone threat intelligence. However, threat intelligence can start to provide a greater level of understanding around the factors which lead to attacks, mitigate the impact of one when it happens, and proactively put in place measures to protect the organization and its infrastructure. Similarly, this article is not intended to be 100% comprehensive in its discussion of threat intelligence themes. Instead, it provides information and guidelines to help build a program or improve their existing setup. It first addresses a problem of definition in threat intelligence, followed by explanations around its usage and application, and concludes by offering advice around implementation and deployment.
Gartner: Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard.
What threat intelligence is not?
Threat intelligence then, is broadly is a collection of enriched or correlated data points about existing or potential threats which can help an organization improve their security. These can be simple technical indicators on one side of the spectrum to in-depth profiles of adversaries on the other – but the key is that they are contextualized and actionable. The use of such a wide-ranging definition means that vendors of all stripes are able to say that they offer ‘threat intelligence.’
There is an argument that this definition is simply too broad, creating confusion in the market. It is helpful to therefore offer some explanation of what threat intelligence isn’t. Data, information and intelligence are too often used interchangeably, and this muddies the waters when it comes to choosing between different solutions.
‘Data’
This is the raw material, often extracted in huge quantities, unstructured and requiring processing before it can be called information, and then intelligence. IOCs are a good example of this: a list of IP addresses or domain names is usually high volume and can be ingested by an SIEM solution to try to make sense of it all. We can’t call it intelligence, however, because the data is not immediately actionable and has no context.
‘Information’
Information is selectively extracted and, when organized, provides more detail for its users than the sum of its parts. If datapoints are simply statements of fact, then information entails a more structured grouping which allows its users to make an analysis of trends or ask questions of it. Still, it is still not immediately actionable, even though it has context, and cannot be interrogated to the same extent threat intelligence can.
What threat intelligence is?
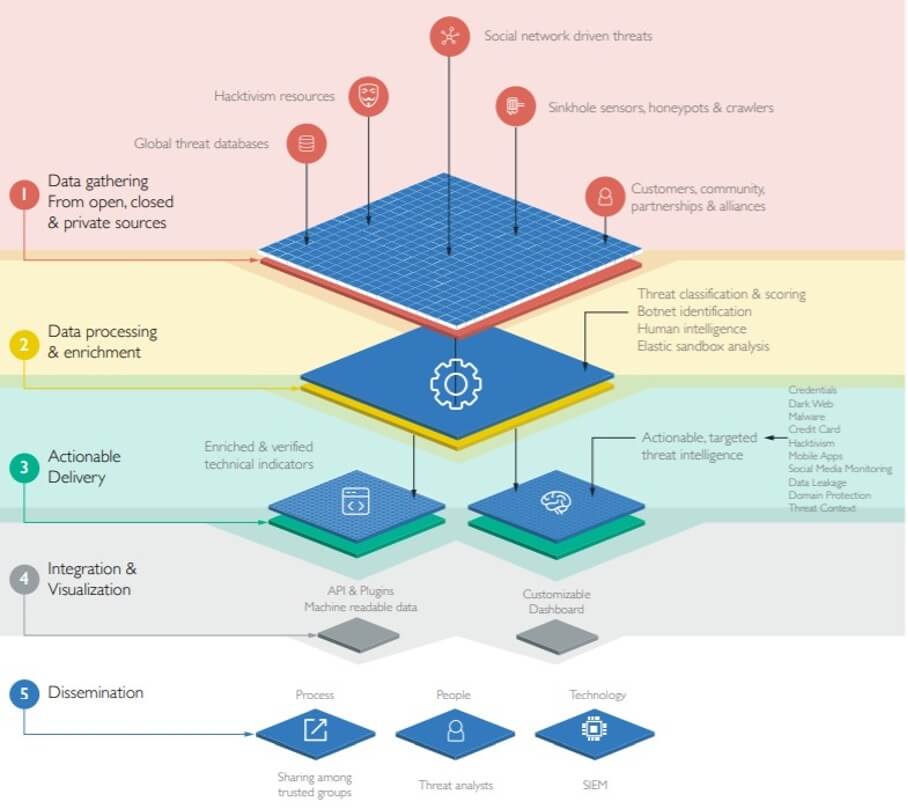
Threat intelligence is what threat data or threat information become when they have been gathered and evaluated from trusted, reliable sources, processed and enriched, then disseminated in a way where it can be considered actionable to its end-user. Source code or JSON files from an underground forum need to be reformatted, for example, or relevant articles need archiving and indexing, in order to make this data and information usable as intelligence. Intelligence means that the end-user can identify threats and opportunities in the cybersecurity landscape, using accurate, relevant, contextualized information. By eliminating the need to sort through thousands of alerts from data, security teams can maximize their own limited resources and accelerate their decision-making processes.
Due to the extraordinarily time-poor nature of their roles, this is where external threat intelligence providers really come into their own. Using automated or manual correlation, internal teams are able to reach out to other organizations to help them prioritize alerts and indicators. Threat intelligence utilized in this way is outlined in the process below.